ABSTRACT Even though the Islamic State of Iraq and Syria (ISIS) has lost its territories and 80% of its revenue base, 30 official and semi-official ISIS channels and chat rooms still emphasize ISIS's longevity and future strength. The sharp decline in the area controlled by ISIS has also destroyed ISIS's ability to collect revenues from oil production, smuggling, taxation, confiscation and other similar activities. ISIS's average monthly income has dropped by 80 percent, from US $ 81 million in the second quarter of 2015 to only US $ 16 million in the second quarter of 2017. Nevertheless, ISIS maintains a strong presence on social media and the internet, promoting its state development efforts – including constructing dams, digging wells, building infrastructure, electrifying villages, and inoculating children – to both domestic and international audiences. ISIS has also used the internet and social media for cyber-terrorism and spreading hatred. They use the internet and social media sites to promote violence as well as provide a network where individuals can learn about deviant behavior from other groups – where they can learn about extremism through association, definition, differentiation, reinforcement and imitation.
Keywords: ISIS, Salafi, Radical, Cyberspace, Virtual, Islam, Syria, Iraq
INTRODUCTION
After the terrorist attacks on the World Trade Center (9/11/2001) in New York, the Bali Bomb in 2002 and other locations, many people in Indonesia and Southeast Asia asked: Why are people willing to commit acts of terror-violence in the name of religion or as terrorists? What are the reasons justifying acts of terrorism in Syria, Iraq, Indonesia and other countries? Who are these terrorists? Where do they target? When will they act? This paper will address these important questions.
Experts provide several assumptions as to why violence in the name of religion is committed primarily by young people. In the era of globalization, borrowing Anthony Giddens’s discourse (2011), many people rely on religious fundamentalism to carry out acts of violence and terror “in the name of God’’.
By means of socio-political, economic and psychological perspectives that see violence and terrorism in the name of religion in the West and Islamic World, including Indonesia, several religious groups (Islam, Christianity, Hinduism, and Judaism) are willing to take violent action against other parties, while at the same time justifying their behavior. Violent perpetrators come from many groups, each with their own reasons – from theological to social to pragmatic; they do not have an adequate basis to argue for their violent actions. (Qodir, 2016).
Consequently, the causes of radicalism-terrorism are many, including political, economic, psychomagical and cultural (religious) factors. (Chaidar, 1999). These become the bases of legitimacy that often appears on the surface when someone observes acts of violence in the name of religion in Indonesia and other countries. Although the reasons vary, one end is violence in the name of religion. (Hanif, 2011; Qodir, 2016).
Here we examine who are the perpetrators of radicalism-terrorism. We have found that what lies behind radicalism-terrorism is the need to ‘defend’ something, whether religion, unfair treatment, discrimination, political marginalization, or cultural marginalization in the era of globalization. The perpetrators feel they have an ideological basis that must be defended against various kinds of injustice, misery, misguidance and violations committed by one group over another (Roy, 1994).
The perpetrators of radical-terrorist acts use the term ‘political representative’ to justify their deeds; that other parties do not feel represented is another problem perpetrators of violence in the name of religion or community think about deeply. In the globalized world, they feel they have a mandate to ‘defend the marginalized’ primarily from the majority religious groups in a country, although sometimes it is not from the majority religious group, but a minority that they feel is discriminating against them (Roy, 2004).
In addition to the ‘profane’ reasons above, perpetrators use a belief in the existence of a religious argument or sacred text to justify their radicalism-terrorism. (Geertz, 1973; Rosaldo, 1988). Although religious texts have multiple interpretations, perpetrators of terrorism and religious violence understand that violence is allowed to be carried out on others as a form of defending religion and even defending God in the name of sacred texts. (Awas, 2001; Muntasir & Fadillah, 2004).
Juergensmeyer (2003), an expert on religious revivalism, writes that there is a fundamental confusion regarding religious doctrine that is understood as the basis of legitimacy for violence against a state that is considered secular (Meyer, 2003). Appleby (2001) agreed that religious sacred doctrines could be interpreted ambivalently in regard to the violence carried out (Appleby, 2001).
ISIS and the West
Former US Secretary of State Hillary Clinton (2014) recognized that the Islamic State of Iraq and Syria (ISIS) movement is a US / Western-made movement to divide the Middle East and destabilize the region; this not only shocked the Islamic World, but also undermined the Islamic World's trust in the US / West in finding solutions to the Middle East conflict.
The US strategy to form ISIS reminds us of the grand design of what is called ‘Rebuilding America's Defenses’ and the Project for the New American Century (PNAC), where the US must rebuild its military and carry out new century projects. One focus of America in the 21st century is to take control of the Middle East. PNAC was conceived and designed by Donald Rumsfeld, Paul Wolfowitz, Dick Cheney and others. In this regard, Hillary Clinton's statement regarding ISIS reaffirms that in Middle Eastern affairs after the Arab Spring, PNAC must proceed according to the grand design of the White House. (Stockbauer, 2003; Sahrasad, 2013)
Consequently, Hillary's recognition that the US government and Western countries deliberately formed ISIS organizations to divide the Middle East is a firm confirmation of the PNAC. Hillary announced the agreement to form the ISIS movement on June 5, 2013.
Hillary Clinton's statement also confirmed the statement of former US National Security Agency (NSA) staff, Snowden (2013), who recently revealed that political changes in the Middle East after the Arab Spring pushed the British, United States and Israel (Mossad) intelligence services to work together to form State guerrillas Islamic Iraq and Syria or Islamic State of Iraq and Syria-ISIS). For the US and its Western allies, a stable and peaceful Middle East is a disaster for the US / Western military industry that is market-hungry, both the black market and the open market. Snowden noted that ISIS has economic resources because it controls a number of oil fields in the eastern region of Syria that reportedly resell oil to the Syrian government. ISIS also mentioned selling antiques from historic sites.
According to Snowden, the US / Western military industrial complex always needs a market worth billions of US dollars to move their economic wheels globally in both black and open markets. The West sources revealed, before taking control of Mosul in June, ISIS had funds and assets worth US $ 900 million, which then increased to US $ 2 billion. The group is said to have taken hundreds of millions of dollars from Iraq's central bank in Mosul. Their finances will be even greater if they can control oil fields in northern Iraq.
Administratively, ISIS had claimed support from people in the US / West who do not want the Middle East to be stable and peaceful. Snowden said the intelligence agencies of the three countries (Britain, the United States and Israel) created ISIS, the largest terrorist organization besides Al-Qaeda, to attract all extremists of the world to one place. They used a strategy called ‘beehive’ that was intended to protect the Israeli Zionist entity by creating religious and Islamic slogans that would trigger an inter-Arab war in the Iraq-Syria region.
Prof. Peter Neumann from King's College London estimated that about 80% of Western fighters in Syria joined ISIS. ISIS claims to have fighters from Britain, France, Germany and other European countries, such as the US, the Arab world and the Caucasus countries. He also claimed that ISIS leader Abu Bakar Al Baghdadi took intensive military training for one year at the hands of the Mossad, in addition to programs in theology and the art of speaking.
ISIS is a terrorist state which spread propaganda through the internet and social media about the ideal Islamic state, which is able to protect the Islamic Ummah. In fact, the cruelty of ISIS to Muslims is extraordinary, not as beautiful as its propaganda. Once again, ISIS is clearly a terrorist creation to destabilize the Middle East, so it makes sense that the history professor, who is also the Director of the Jakarta Islamic State University (UIN), Graduate School Prof. Dr. Azyumardi Azra, stated that the presence of ISIS contains more potential to be opposed by the majority of the World Muslims (Ummah Islam) because it is related to religious understanding which is far more extreme than Wahhabism.
Azra (2014) alleged that ISIS's religious ideology destroyed many of the mosques in the area they occupied on the grounds that the mosque became a place of worship that reeks of polytheism that is contrary to the belief in monotheism. This understanding also intends to destroy the Kaaba in Mecca which according to them has become the center of worship of polytheism. It is certain that the emergence of ISIS was related to instability in the politics and security of Arab countries. Referring to the theory of political sociology, he said, when the state was weak - unable to maintain political stability and security - non-state actors and groups took advantage of the lack of state power to dominate these areas.
Since World War II, the Arab World or the Middle East as a whole has been one of the most unstable regions in the world; it has been the center of continual political upheaval and violence. The main factors are the Palestinian-Israeli conflict, the struggle among Arab countries themselves, and domestic political conflicts in many Arab countries between authoritarian regimes and Islamist movements, such as the Muslim Brotherhood and its various splinter groups and Salafis.
Power and strength of social media
Social media (Social Media) is an internet-based online media that allows users to interact virtually (in other terms, it is often called cyberspace: dumay, acronym of dunia maya, cyber-space). Social media includes accounts to share photos, videos and status updates, as well as to greet and meet each other virtually. The internet, social media and multimedia technology become a unit that is difficult to separate and pushes on new things. The Salafi radicalism of this century creates and unfavorable image of Islam, and connects Islam with violence, thus harming the Islamic world in general, even though Islam is a religion that is rahmatan lil alamin, grace and mercy to the universe. The birth of Islam thousands of centuries ago was not even colored with swords; Islam brought messages of peace brought by the Prophet Muhammad. It also labeled radicalism as a very negative understanding. Two main things can be concluded:
First, internet media plays a very large role in providing information to the public, especially introducing young people to radical ideology. This is compounded by the fact that the recruitment of young people in radical organizations is mostly done using internet media. The fact that terrorist organizations and affiliates have used technology to more easily spread propaganda and recruit potential members through the internet is a very sad outcome in the progress of mass media itself.
Second, mass media plays a key role in deterring and providing information to the public on issues of radicalism, so that the public can take precautionary measures to develop extremist movements starting from their own environment.
Numerous Muslim extremists used the moment and the media to spread the ideology of their jihad. Therefore, all ideas of radicalism and terrorism are spread easily using technological advances. In the Muslim community, the term Virtual Islam was born. Through the internet, many radical groups have expressed their own interpretations of Islam and the principles relating to Islam. This has serious implications for the variety of material and perspectives available, and for how randomly this information can be accessed. One's first experience with Islam in cyberspace is perhaps what is called fundamentalist Muslim groups and organizations as a mainstream with orthodox interpretations.
The results of John Obert Voll's research on terrorist networks are no longer the most important link in the struggle by transforming the politics of Muslim communities around the world, but intellectual networks and the exchange of ideologies through the internet (email) (Voll, 2011). One pattern of terrorism in Southeast Asia and Indonesia uses cyberterrorism, namely the use of computers and internet networks by terrorist groups in carrying out their actions, such as using internet media for the process of radicalization, breaking into financial systems, and controlling systems of transportation equipment, such as trains and airplanes. Imam Samudra became active in cyberspace ahead of the blast of the Bali II Bombing, since June 2005, until it was moved to Nusa Kambangan. In the Bali Bomb II, Noordin M. Top and Abdul Azis built a special site to coordinate all related activities in carrying out acts of terror. Max Fiderman created the anshor.net site with a credit card.
The strength of the internet lies in its paradox and contradiction. Because, cyberspace is a virtual space that is formed through networks between computers. (Sageman, 2004), when wandering in it, we will find various panoramas full of paradoxes and contradictions: pleasure-fear, goodness-evil and truth-falsehood. The paradox of cyberspace is indeed the same as paradoxes in the real world, but it is extreme, strong, direct and intense.
Zaleski (1997) presents a map of thoughts behind cyberspace by showing various ideas, including paradoxes from various cyberists, cyber religionists and cyber programmers. They are optimistic about the new reality of cyberspace, which can replace the existing reality and become a kind of new religion, new spirituality and new God. In addition, Zaleski described their fatalist attitude in dealing with various bad and frightening sides of the new world.
Conversely, Zeleski displays a map of cyberspace users by various real religious groups (Hinduism, Buddhism, Judaism, Christianity, Islam), and how this new world is used as a means of spreading religious teachings, communicating between religious people, and even as a channel of spiritual energy. He shows how cyberspace is a positive and effective tool for the reality of diversity in this global society.
Slouka (2010), a critic of American culture, is very cynical about the people behind information technology; he makes scathing criticisms of the philosophers and ideologies behind the technology of cyberspace that instill the self-religionists, people who have an obsession to be God. They are people who believe the world of the mind can be loaded (simulated) in a computer. They also believe the future of humans is not in RL (Real Life) but in various forms of VR (Virtual Reality) – even believing cyberspace is a form higher than spirituality.
They use computer technology to create a kind of prophetic movement according to their version. In such conditions, as Judge Bey said in The Information War, Media (cyberspace) takes over the role of religion (priest), in his duty to give humans a way out of the body by redefining spirit as information. However, the essence of information in cyberspace is an image whose abstract form seizes the primacy of body principles and stops it with the principle of bodyless ecstasy. The Islamic radicalism movement that has emerged on virtual networks – Facebook, YouTube, Twitter, Tumbler, and free application services like WhatsApp – have become spaces for new ways to conduct propaganda, recruitment, training, planning, and invitations to the establishment of the Islamic Khalifa. The current strategy that continues to be practiced by ‘defenders of Islam’ influences the way of thinking of Muslim societies. They actively use social media by targeting young people as the majority of citizens on netizens.
At this point, the Islamic online media platform of the State of Iraq and Syria (ISIS) processes and mixes graphic audiovisual content with religious-ideological writings to justify violent terrorist tactics. In recent years, ISIS jihadist groups have grown and developed its propaganda to work on open API (Application Programming Interface) platforms such as Twitter®, Facebook®, YouTube®, and Tumblr®.
Radical Salafism
In recent developments in the Middle East, radicalism among the Salafists has surged sharply, as evidenced by the rise of the Islamic State of Iraq and Syria (ISIS). So far, the Jihadist Salafists and Takfiri have formed the Islamic State of Iraq and Syria (ISIS).
We should note that since declaring its caliphate in June 2014, the self-proclaimed Islamic State has conducted or inspired more than 140 terrorist attacks in 29 countries other than Iraq and Syria, where its carnage has taken a much deadlier toll. Those attacks have killed at least 2,043 people and injured thousands more. (Sahrasad & Chaidar, 2019)
Although ISIS has recently lost territory and 80% of its revenue base, 30 official and semi-official ISIS channels and chat rooms still emphasize ISIS's longevity and future strength. The sharp decline in the area controlled by ISIS has also destroyed ISIS's ability to collect revenues from oil production, smuggling, taxation, confiscation and other similar activities. As a result of ISIS's destruction, ISIS's average monthly income has dropped by 80 percent, from US $ 81 million in the second quarter of 2015 to only US $ 16 million in the second quarter of 2017. Nevertheless, ISIS maintains a strong presence on social media and the internet, promoting its state development efforts – including constructing dams, digging wells, building infrastructure, electrifying villages, and inoculating children – to both domestic and international audiences.
ISIS has also used the internet and social media for cyber-terrorism and spreading hatred. They use the internet and social media sites to promote violence as well as provide a network where individuals can learn about deviant behavior from other groups – where they can learn about extremism through association, definition, differentiation, reinforcement and imitation.
The Salafi or Salafiyah movement has spread throughout the world, including Indonesia and Southeast Asia. A number of Muslim leaders continue to spread the movement, including Ibn Qayyim Al-Jauziyah, Muhammad bin Abdul Wahab, Jamaludin Al-Afghani, Muhammad Rashid Rida, Sir Ahmad Khan, and others. According to the Islamic Encyclopedia, a number of Islamic organizations in Indonesia, such as Al- Irshad, Muhammadiyah, Persis, and Islamic Community Unity are based on the Salaf movement. Thousands of radical Salafist have used the internet and social media, as illustrated in Figures 1-3. Yusuf al-Qarāḍāwī and his colleagues in the European Council for Fatwa and Research, who were influenced by Salafi-reformers, such as al-Shawkānī, al- Afghānī, 'Abduh and Riḍā, who valued text and modernity, encouraged this use of the internet and social media (Rusli, 2014)1
Table 1. The Appearance of the Site of Islam Online1.
Sources: Al-Jāmi‘ah: Journal of Islamic Studies Vol. 52, no. 1 (2014), p.210.
Table 2. Variables used by Marc Sageman.
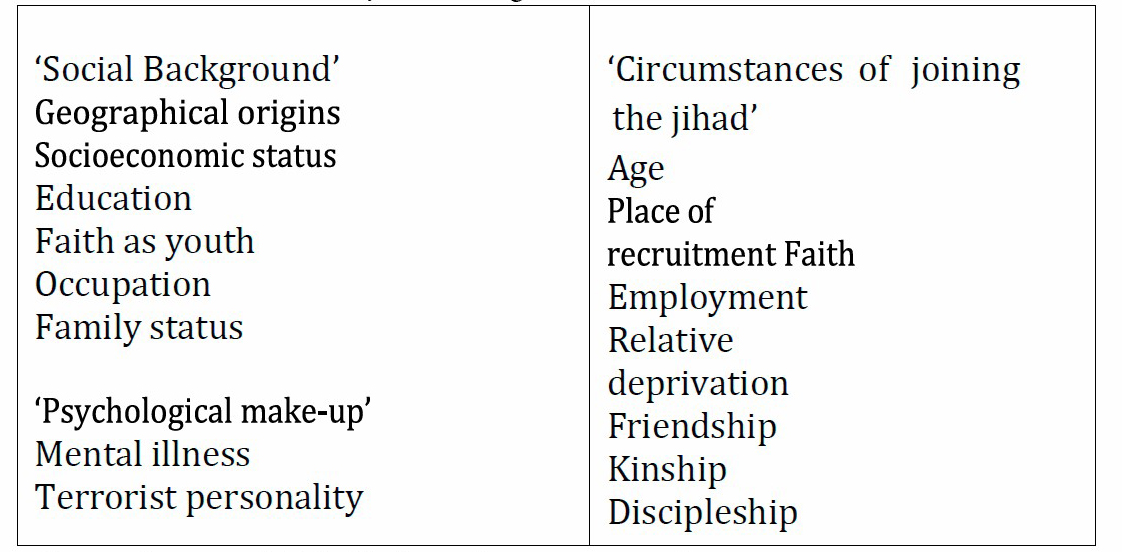
Source: Sageman (2004), Understanding terror networks.
It is not easy to answer the question: why do people join terrorist groups? In Sageman's (2004) search for common features to explain why individuals engage in jihadist terrorism, he investigated seventeen variables. These variables are divided into three general categories: ‘social background’, ‘psychological makeup’ and ‘state of joining jihad’ (Figure 1). In this context, Bloom and Daymon (2018) caution that ISIS’s use of peer-to-peer encrypted messages shows no signs of declining, despite predictions that the group was vanquished and would cease to exist.
ISIS elites and leaders are aware that platforms such as Twitter and Facebook are continually monitored, and face aggressive elimination of accounts. Given these risks, ISIS has selected Telegram as its preferred platform for spreading propaganda and recruiting new members. Research has investigated how Telegram has been used by ISIS and its supporters and has assessed what kind of threat Telegram use might create when ISIS transitions to a ‘Virtual Caliphate’.
The ISIS elites and leaders are aware of the use of social media, the internet, and new technologies, including their risks, as seen in their use of an encrypted platform as the main means to radicalize, recruit and plan. As Kello (2017) from Oxford University said, in the virtual domain, vital strategic operations can be ‘shrouded in secrecy’, causing difficulties for scientific research, security forces, defense operators and policy makers to track them down. ISIS terrorists succeeded in attacking Europe as shown in Figure 1.
Figure 1. Jihadi terrorist networks in Europe and their plots and attacks (September 2001 - August 2006).

Sources: Hidde Donker & Edwin (2006), Jihadi terrorists in Europe, Netherlands Institute of International Relations, Clingendael.
ISIS elites and leaders understand that individuals shape their perceptions of themselves based on identification with groups, core group values, and their emotions. As a result, the continued presence in the online environment can encourage extreme political and religious views, excessive violence, and competition outside the group. In fact, ISIS also creates a spatial echo for radicalization. Among social media and internet sites, Telegram applications are increasingly in demand as a platform of choice for clandestine activities of ISIS and its supporters.
The uniqueness of Telegram in terms of privacy and security helped it reach 100 million users in 2016. Telegram is commonly used by ISIS terrorists to recruit and coordinate attacks, including in Brussels, Belgium, 2017. The perpetrators of attacks in Paris in 2015, attacks on New Year's Eve 2017 in Turkey, and attacks in St Petersburg, Russia in April 2017 also used Telegram. In Indonesia, a number of terrorism suspects who were arrested in December 2016 claimed to have learned to make bombs by following directions via Telegram. ISIS elites and leaders understand that Telegram cannot be traced after an attack.
Initially, most of ISIS’s propaganda focused on developing the Islamic State, both physically and figuratively, offering ‘supra-national brands ‘Khilafah’’ (Virtual Caliphate) as legitimizing and moral reasons for their actions and existence. Projections of state buildings are intended to create attractive options for prospective immigrants, but also for the ISIS transition from the rebel movement to the formation of a distinctive ‘Islamic State’, and ‘Virtual Caliphate’.
Even though it is a Virtual Caliphate, ISIS continues to operate in many areas, including doctrinal militaristic efforts, strategic communication, civil-military relations, engagement of key leaders, supporting operations, and military fraud. (Gambhir, 2016). ISIS uses this internet capability in physical capacity with respect to the local population and in digital capacity through global communication to their networks and main supporters. ISIS also utilizes operational security, electronic warfare, and cyber operations in various parts of the world.
Thus, it is clear that even though ISIS has been defeated and cornered due to losing a lot of territory, ISIS is still able to build a 'Virtual Caliphate' that is capable of moving globally and disseminating its agenda, vision and mission to the domestic and international community. Indonesia must not be complacent, and must continue to be vigilant in anticipating the development of terrorism by the Virtual Caliphate and its networks and cells in various parts of the world, including in Southeast Asia. Moreover, it is very possible that ISIS members and sympathizers are in the area around us and are targeting us to be part of their Virtual Caliph's territory.
From books to virtual world
The existence of social media intensified the war, while at the same time expanding the influence of the teachings of the movement that was spread to the community. In this situation, the state can force its citizens to adopt the state's ideology, while each individual has their own ideology; then there is attraction between personal ideology on the one hand and communal ideology on the other. A position needs to be taken against the clash of ISIS ideologies that are disturbing the existence of the Indonesian Republic:
First, Anticipatory, namely fortifying and confining the teachings and flow of the ISIS movement so as not to expand and become massive in the midst of society. (Zada, 2011)
Second, Comprehensive, by always instilling Islamic values that are rahmatan lil alamin to all components of the nation through imaging and positive information content, especially on social networks.
Third, Educative, by conducting an educational movement against religious radicalism starting from the level of early childhood education through to tertiary education.
Fourth, Participatory, cooperating with all elements of society to be actively involved in counteracting the spread of ideology and the teachings disseminated by ISIS followers, both from the path of social media, television media and other media. (Lister et al., 2018).
Anticipatory efforts on the widespread influence of the ISIS movement through social media were carried out by massively campaigning on various bad news addressed to ISIS. This was done so that there was an awareness that the ISIS movement must indeed be avoided and shunned by all groups; it also serves to narrow the space for ISIS in Indonesia.
The internet is able to combine new media forces and political aspirations that Kahn and Douglas (2004) say will be increasingly popular and entrenched in the future, where the growth of users is fast and difficult to predict with a variety of facilities provided to produce material and models of democracy. There are more than 30 million internet users in Indonesia and the user growth rate is around 12.5 percent per year (internetworldstats.com). Indonesia is also ranked 7th in the world in Facebook use; when this article was written, there were nearly 11.8 million Facebook accounts among users 18-34 years old.
The virtual world has become important in shaping thoughts, behaviors, and deeds, as well as the basic needs (styles) of human life. Terrorist groups continue to use the internet and social media to grow and spread their interests. Gabriel Weimann's research shows that the network of terrorist groups is increasingly attentive to the use of cyberspace. This can be seen from the number and variety of sites managed by jihadi groups, which have increased from year-to-year by 2,650; jihadist groups managed more than 9,800 sites in 2014. Weimann emphasized that the virtual world offers many advantages for terrorist groups (Weimann, 2015), including easy access, lack of binding controls and regulations, wide audience, anonymity, and speed of information flow; it can be used as an interaction medium, it is very cheap to create and maintain, it offers multimedia (print, sound, photo and video) that remain its main purpose – as such, the internet has become a mainstream media source (Orbis, May 2018). In addition to the continued growth in numbers of radical sites, it is very important to pay attention to the significant development of the form and the pattern of terrorism itself.
There are at least three stages of development in the form and pattern of the spread of the notion of terrorism in this virtual world. The initial stage focuses only on the dissemination of ideology through website facilities. The second stage uses interactive features, such as the creation of forums and chatrooms. The third stage uses social media, such as YouTube, Facebook and Twitter; this is increasingly popular.
Gabriel Weimann said terrorist groups have shifted to the realm of social media for the purpose of building interaction, appearing more trendy and popular, and to better reach their demographic target. Responding to the strong influence of the internet, social media has been used as a medium for learning attitudes of intolerance, radicalism, and suicide bombings. A study conducted with the Brooking Institution and Google Web, published by the New York Times, identified 46,000 Twitter accounts associated with ISIS propaganda; Twitter blocked 125,000 ISIS-like accounts at the end 2014. ISIS accounts on average have more than 1,000.32 followers.2
2A Pew Research Center survey in 2015 showed that in Indonesia about 4% (10 million people) of the population supported all forms of ISIS actions; the most support was among young people. Compare the results of the Setara Institute surveying 684 students from 114 Middle Schools Public (SMU) in Jakarta and Bandung to find out the views of students about the ISIS movement.
Across the Muslim world, the rise of radical Salafism is getting stronger after Al-Qaeda attacked the New York World Trade Center (WTC) on September 11, 2001, killing more than 12,000 people. (Juergensmeyer, 2003; Hoffman, 2006). This Salafi terrorist act marked the beginning of a new era in the post-Cold War terrorism movement, an Islam-based terrorism movement. Islam is in the spotlight of the world because, in reality, acts of terrorism involve a number of individuals or organizations that contain Islamic meanings and symbols of Islam are very attached to acts of terrorism (Hasan, 2008).
As a result, the study of terrorism is important, because terrorism has had extensive consequences, not only politically and militarily, but also economically. This September 11, 2001 attack was followed by a series of suicide bombings in Bali in 2002, Madrid in 2004, London in 2005, New Delhi in 2005, and Mumbai in 2006. Suicide bombings also occur in conflict zones such as in Iraq, Kashmir, Sri Lanka, Israel-Palestine and other Middle East countries. The radicalism of Salafists in the WTC bombing of September 11, 2011 ushered in a new era after the Cold War which considered terrorism to be synonymous with Islam (Sahrasad, 2013).
CONCLUSIONS
The terrorism movement is no longer a secular organization, such as the Japanese Red Army (JRA), the Tamil Tigers in Sri Lanka, the Red Brigade in Italy, and others. Instead, the terrorism movement is now synonymous with Islam, such as al-Qaeda, ISIS and Jamaah Islamiyah. Today, the Islamist-based terrorism movement is a real threat throughout the world, including in Indonesia. Terrorism has political motives and goals, political claims and political struggles. Terrorism is a notion that to achieve goals, various methods including violence, intimidation and murder are justified. Indeed, terrorism is not solely based on religious factors, but also on factors of economics, politics and history that are closely linked in the search for identity amid the current of modernization and globalization.
Many people consider this categorization a Western creation intended to divide Muslims and prevent Muslims from unifying and advancing. Therefore, it is not strange that when the Bali I bombing by radical Salafists occurred in 2002 (killing some 200 people from 20 countries) and the Bali Bomb II occurred, many Salafist leaders stated that the terrorists were only ‘fictional’ Westerners trying to damage the image of Islam by always associating it with terrorists and violence.
However, the terror incidents in Indonesia continued, followed by the arrest of terrorists (pro-Al Qaeda or pro-ISIS); we witnessed other facts in the form of networks and testimonies formed by them. In Indonesia and Southeast Asia, it is possible that the biggest threat is not from Salafist radicalism or Islamic terrorism (the number of followers of Islamic radicalism in Indonesia and Southest Asia is relative small compared to the majority of peace-loving Indonesian Muslims), but the biggest threat comes from global information technology – the internet and media that is exploited and used by the radical Salafist, and increasingly out of governmental control, while the IT community and social media companies themselves do not develop a strong self-control system.
It should be noted that there are indeed radical Salafists who dedicate their lives to being terrorists, teach terrorism, galvanize potential terrorists, and convince people to follow a terrorist-style understanding of Islam. From this phenomenon, we can say that radicalism and terrorism are not purely Western creations, but are real facts among the Salafist Muslim because there are those who believe, embrace, and develop them from among the Muslims themselves.
REFERENCES
Appleby, R.S. (2001). The ambivalence of the sacred: religion, violence and econciliation. Journal of Law and Religion, 16(2), 975-979. https://doi.org/10.2307/105176
Azra, A. (2014). Tentang terorisme, Kompas, 05.
Awas, I. (2001) Khilafah made in yogya dalam risalah kongres mujahidin 1 danPenegakan syariah islam. Yogyakarta: Wihdah Press.
Bloom, M., & Daymon, C. (2018). Assessing the future threat: ISIS's virtual caliphate, journal Orbis, 372-388. https://doi.org/10.1016/j.orbis.2018.05.007
Chaidar, Al. (1999). Konsepsi nation and character building dalam pemikiran SM kartosuwirjo: reinterpretasi dan redifinisi makna integrasi pangsa, proceeding of seminar Sejarah di UI, Depok.
Clinton, H. (2014). Hard choice. New York: Amazon.
Giddens, A. (2011). Runaway world. New York: Profile Books.
Geertz, C. (1973). The Interpretation of cultures. New York: Basic Books.
Gambhir, H. (2016). The virtual caliphate: ISIS 's information warfare. Washington DC: Institute for the Study of War.
Hanif, M. (2011). ISIS dan Kekerasan Keagamaan di Timur Tengah, Jurnal Kajian Islam dan Keindonesiaan. IAIN Salatiga, 9(2).
Hasan, N. (2008) Laskar jihad: islam, militansi, dan pencarian identitas di Indonesia pasca-orde baru. Jakarta: LP3ES & KITLV Jakarta.
Hoffman, B. (2006). Inside terrorism. New York: Columbia University Press.
Hidde Donker, T., & Edwin, B. (2006). Jihadi terrorists in Europe. Netherlands institute of international relations: Clingendael.
Juergensmeyer, M. (2003). Terror in the mind of God: the global rise of religious violence (comparative studies in religion and society) (3rd ed.). London: University of Californai Press.
Kello, L. (2017). Virtual weapon and international order. New Haven: Yale University Press.
Kahn, R., & Douglas K. (2004). New media and internet activism: from the ‘battle of seattle’ to blogging. New Media & Society 6, 87-95. https://doi.org/10.1177/1461444804039908
Lister, T., Ray S., Mark B., Sean O., Michael H., and Mohammed T. (2018, February 12). ISIS goes global: 143 attacks in 29 countries have killed 2,043. CNN report.
Meyer, I.H. (2003). Prejudice as stress: conceptual and measurement preblems. American Journal of Public Health, 93(2): 262-265. https://doi.org/10.2105/ajph.93.2.262
Muntasir, M., & Fadillah, A. (2004) Aplikasi Islam dalam Wilayah Kuadran, buku terbitan Jakarta: Pillar Press.
Neumann, P. (2015) Bagaimana kelompok jihadis ISIS terbentuk? (How was the ISIS jihadist group formed?). Retrieved April 2,2015 from https://www.bbc.com/indonesia/dunia/2014/07/140725_profil_isis and https://news.detik.com/internasional/2652753/tentang-isis-dan-teori-konspirasi-yang-menyelimutinya?nd771104bcj=
Qodir, Z. (2016). Kaum muda, intoleransi, dan radikalisme agama. Studi Pemuda, 5 (1).
Roy, O. (2004) Globalized islam: the search for a New Ummah. Columbia: Columbia University Press.
Roy, O. (1994). The failure of political islam. Massachusetts: Harvard University Press.
Rosaldo, R. (1988). Ideology, place, and people without culture. Cultural Anthropology 3(1), 77-87. https://doi.org/10.1525/can.1988.3.1.02a00070
Rusli, R. (2014). Progressive salafism in online fatwa, Al-Jāmi‘ah. Journal of Islamic Studies, 52 (1), 205-229. https://doi.org/10.14421/ajis.2014.521.205-229
Stockbauer, B. (2003). Rebuilding America's defenses and the project for the new American century. Retrieved June 18, 2015 from https://www.antiwar.com/orig/stockbauer1.html
Sahrasad, H. (2013). Arab spring: risalah studi timur tengah. Indonesia: CreateSpace Independent Publishing Platform.
Sahrasad, H., & Chaidar, Al. (2019, January 11). Alert on IS must continue, opinion. The Jakarta Post Daily.
Sageman, M. (2004). Understanding terror networks. Philadelphia: University of Pennsylvania Press.
Slouka, M. (2010). Essays from the Nick of time: reflections and refutations. Minnesota: Graywolf Press.
Snowden, E. (2013). 10 “Dosa esar” NSA yang dibocorkan edward snowden. Retrieved April 29, 2015 from https://www.liputan6.com/tekno/read/2185425/10-dosa-besar-nsa-yang-dibocorkan-edward-snowden
Voll, J.O. (2011). The middle East in world history. Oxford Handbooks online: Oxford University Press. https://doi.org/10.1093/oxfordhb/9780199235810.013.0025
Weimann, G. (2015). Terrorism in cyberspace: the next generation. United States: Woodrow Wilson Center Press and Columbia University Press.
Zada, K. (2011). Wajah enerbitan Islam di Indonesia radikal. Indo-Islamika, 1(1), 1 -19.
Zaleski, J. (1977). Spiritualitas cyberspace: bagaimana teknologi komputer mempengaruhi zada, khamami. Wajah Penerbitan Islam di Indonesia Radikal, 1(432), 1 -19.
